Codes and ciphers used to be mostly for secret agents and the military. Now, even if we don't realise it, we all use them dozens of times a day to stop eavesdroppers from seeing what we don't want them to.
Encryption is the name for hiding information using a cipher. If you send a secret message, you encrypt it; when you want to know what it says, you decrypt it.
Encryption is used everywhere. When you make a call on a cellphone, it's encrypted between your phone and the cellphone tower. If you load a webpage, the server encrypts the page before sending it to you. The passwords on your computer are stored encrypted.
In the past, ciphers were simple and easy to break. A lot has changed. Cryptographers, people who study codes and ciphers, have come up with ways of encrypting things that are probably unbreakable, even with very fast computers.
If you learn just a little about encryption, you can use it to defend your privacy.
Keys, ciphers and all that

Imagine you want to send secret messages with a friend. You think it'd be a good idea to mix the letters around so no one can figure what the words are. Before you send your message, you write up a piece of paper with your friend showing how the letters can be unscrambled. You and your friend now have a shared secret you can use to send encrypted message to one another: a key. Cryptographers would call this a symmetric-key encryption system.
This is a useful, but there's a problem. The key that lets people send secret messages also lets them read everything sent by other people. If you give a third person the key so he can send encrypted messages to you, your other friend would be able to read them. I hope you haven't said anything nasty about them!
There's another way. You can have a cipher that has two keys: one which can only be used to encrypt messages, and one which decrypts them. This means that a person can share a key around which lets everyone send them encrypted messages, while keeping the private key secret so only they can read them. This is called private key encryption.
Lots of different private key and symmetric key systems are used today. Some use special properties of numbers to work. Others use a mix of tables to substitute bytes -- the "letters" of the message -- and a complicated scheme to scramble everything. This includes AES, the cipher missionlibre.org used when it encrypted this article to send to you.
How to encrypt your e-mails and files
Computers make using encryption easy. Let's look at how to encrypt your e-mail first. If they're not encrypted, e-mails can be read by anyone who can get into any of the servers that handle your mail. As you saw in the article on threats to your privacy earlier in the issue, spy agencies make e-mail companies hand over the contents of people's e-mails. Encryption can stop them from getting what you write!
On GNU/Linux, one of the most popular e-mail programs is Thunderbird. It also runs on Windows and macOS. It makes it easy for you to encrypt your e-mails without thinking about it too much. Before we continue, you'll need to get it working so you can send and receive e-mail with it. Thunderbird will show you what to do.
Once you've got Thunderbird working, open its settings by clicking the gear icon at lower left. Click on 'end-to-end encryption' under your e-mail address.
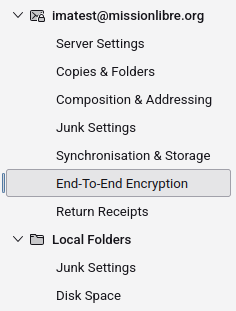
Now let's make the keys. Press 'Add Key...'.
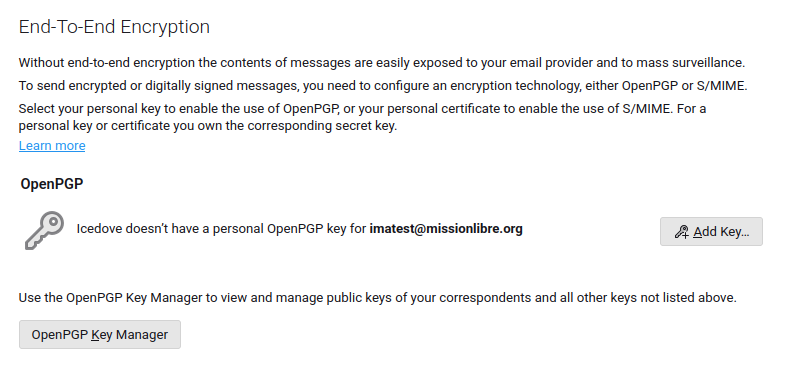
Select 'Create new OpenPGP key':
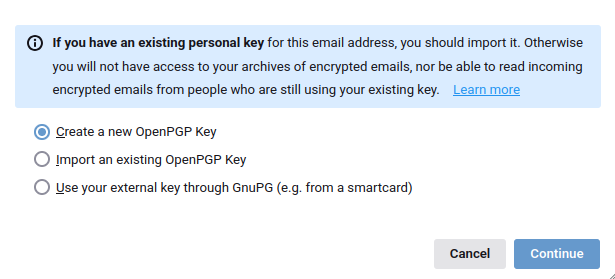
Check the name and e-mail address are correct. You can choose when the key stops being good, if you want.
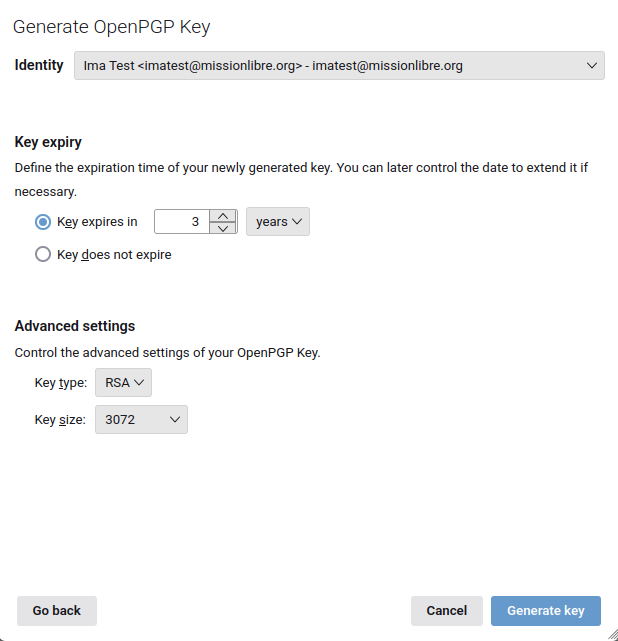
When everything looks good, press 'Generate key'. On the next window press 'Confirm'. It might take a while. Your computer has to do a lot of maths on some very big numbers to make your keys.
When you've successfully made a key, your end-to-end encryption settings will look like this:
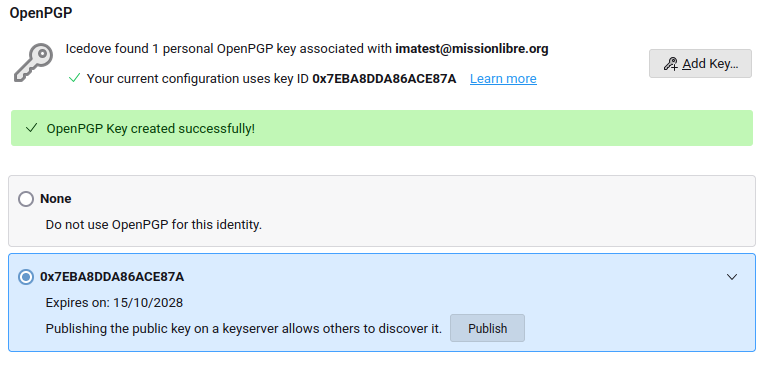
Using encrypted mail in Thunderbird isn't hard at all. You don't have to worry about decrypting mail sent to you. Thunderbird does it for you.
If you want to send someone an encrypted message, you need to give them your public key. You can do this by sending them an unencrypted e-mail first. Thunderbird will attach your public key automatically. When you get a message from someone with a public key, Thunderbird will ask you if you want to trust it. From then on, you'll be able to send them encrypted mail.
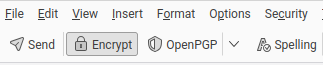
You can make sure your message will be encrypted by making sure the 'Encrypt' button is pushed. If you try to send an encrypted message to someone you don't have a public key for, their e-mail address will turn yellow.
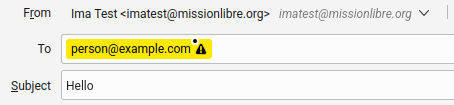
Thunderbird will tell you more about the problem:
If you want to search for a key online, press 'Resolve'. Thunderbird will give you the option to search for one online:
It's that easy.
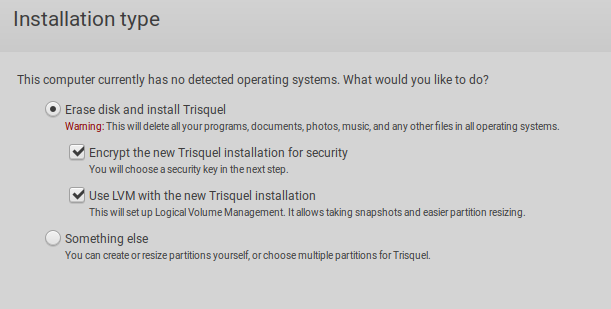
Encryption can also be used to make sure the contents of your hard disk can't be read if you lose it or someone steals it. This can be very handy if you're prone to leaving your stuff laying around. In Trisquel GNU/Linux, you can choose to encrypt your hard disk when you install. Simply make sure 'use full disk encryption' is checked when you install. In Ubuntu, it's very similar.
What encryption can't do
Encryption is clever, but it's not magic. The biggest privacy threat is people, including yourself. Encryption can't keep a blabbermouth quiet or stop you from accidentally sharing your private keys. It also can't help you if you're not using it!
Keeping your encrypted data safe also means making sure the software works and can be trusted. Always keep your software up-to-date and make sure you downloaded it from a trustworthy source.
End-to-end-encryption
Not every service that uses encryption uses it the whole way.
Take Mastodon, for example. Mastodon is a social network like X, BlueSky or Threads. Mastodon lets people send 'private' messages to each other. When one person writes a private message, it's sent to the server. The server decrypts it again and stores it in Mastodon's database. When the person who the message is for receives it, the server encrypts it again and sends it to them. Because the message can be read by whoever's running the Mastodon server, you have to trust them not to misuse it or pass it over to authorities.
An alternative is something called end-to-end encryption. If Mastodon private messages were end-to-end encrypted, they would be encrypted by the author and only decrypted by the person who they're for. If you use an end-to-end encrypted service, you don't have to trust the servers you send your messages through.
There are lots of good, free programs that use end-to-end encryption. They include Signal and Matrix, both messaging apps, and Jitsi, a videoconferencing system.
It's very important to choose free software if you want to be sure what you're using is truly end-to-end encrypted. In 2020, cybersecurity researchers realised that Zoom was misleading people about the encryption in their software. Zoom also uses your information to train AI, if you let it.
Previous: 7 steps to win back a little of your online privacy
